
Azure Tags are an excellent tool for Azure Administrators and end-users. We can assign them to our resources so we can easily identify them, or apply automation based on tags. As such they indispensable part of Azure Governance, but in order to stay useful and clean, they also require governance of their own.
Each resource can have up to 50 assigned tags. That’s a lot. Too many tags can make more harm than help. If we try to force many tags on every single resource means that they will become useless and repeatable. We can also end up entering the same information in different tags.
But even if we keep our tags list short and clean, we define our tagging strategy as part of our Azure Governance, and well document everything, tags can still get messy. They are text fields, and if we allow users to enter information manually that text will be inconsistent. Users can add unnecessary tags, or miss important ones, enter values in a different format, or a different order.
Few tips on how to keep tags clean:
Teach users how to use Azure Resource Tags
Using tags can help users to understand their power and how that can make their work easier. Once they realize that, next time they create some new resource, they will not skip Tags blade without entering anything.
Using tags doesn’t mean just going to a resource and then reading the individual tags for that single resource.
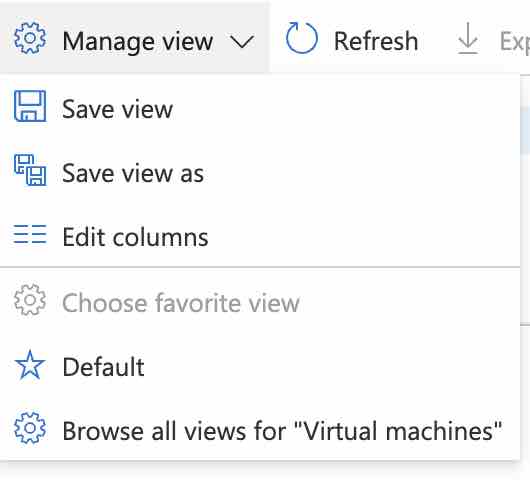
Did you know that you can add tags or an individual tag to almost any view in Azure Portal? If you open Virutal Machines, for example, you can go to Manage View -> Edit Columns, and select Tags, or an individual Tag. Easy and very useful.
Tags can be part of various automation solutions. You can run deployments based on assigned tags, or run scripts to perform various tasks. As inspiration, take a look at my article about How to use Tags to perform Azure VM Start-Stop on a schedule.
You can include tags in your Infrastructure as Code templates.
Utilize Azure Policy
Azure Policy is a powerful tool that we can easily utilize to help us with our tagging strategy. Azure includes many built-in policies that we can simply apply, many of which are related to Azure Resource Tags.
Here are some example scenarios:
- Enforcing a specific tag on a specific resource type. For example, we want to make sure that each resource group has an Environment tag assigned
- Allowing only specific values for the tag value. We want to make sure that only specific values for the specific tags are allowed
- Auditing if specific tags are assigned, so we can add it if missing
- Automatically assigning specific tags directly, or making resources inherit the tag and its value. For example, we can automatically assign the creator tag or time of creation to each resource. Or inherit tags from a Subscription or a Resource Group, down to resources.
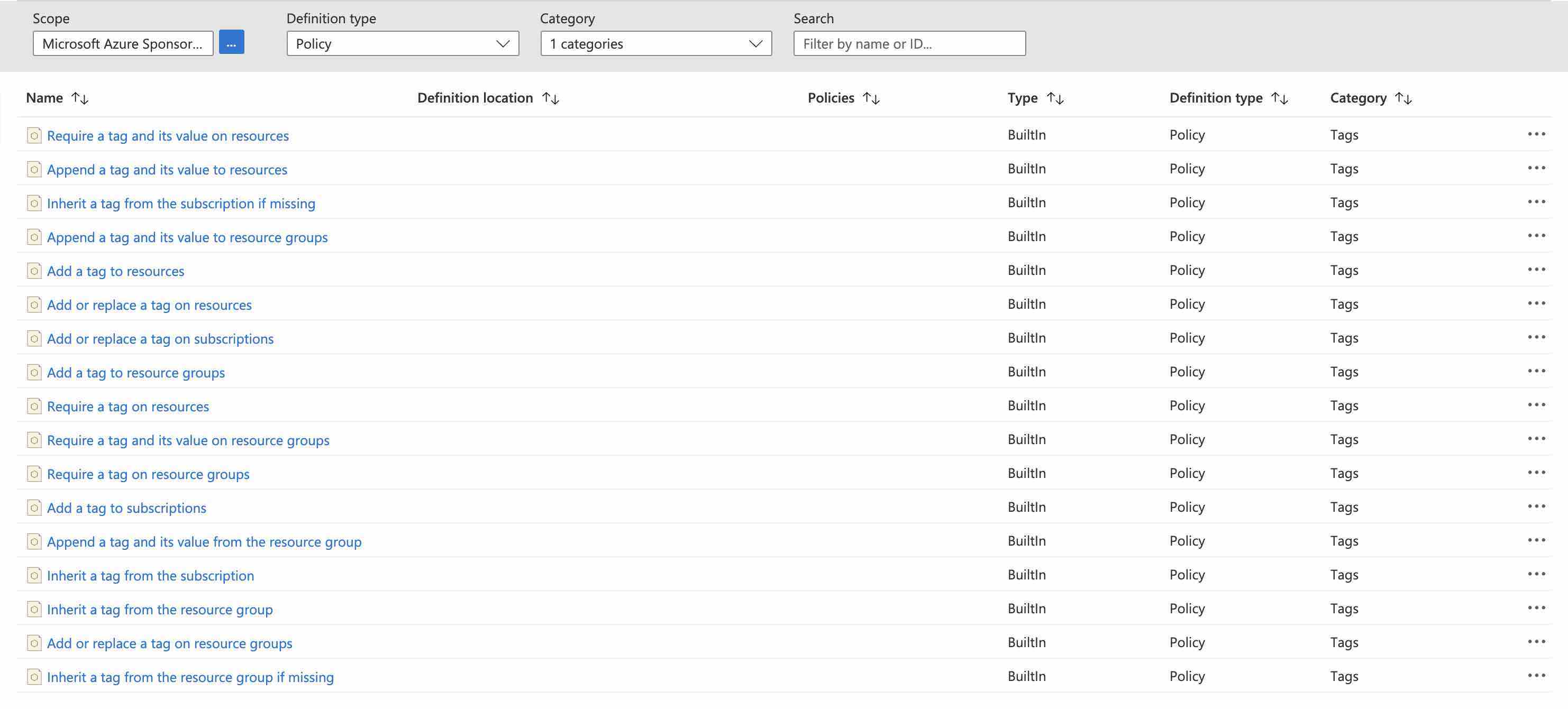
You can see that Azure Policy can help us with automating our tags and keeping them clean.
However, too much power and enforced configurations can also introduce issues and deployment failures. Sometimes it’s not possible to enter tags during resource creation. Some processes within Azure itself create temporary resources before creating the final resource, and this can also fail if we don’t allow specific resource types to be created without assigned tags.
Clean up your Azure Resource Tags
There is a big chance that we will end up with typos or inconsistencies in tags names or values sooner or later. Here are a few examples of what can go wrong:
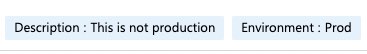
The tag Name is correct, but the tag Value is not
This situation can occur when you configure Tag, but you don’t verify the Value of it by the Policy.
As an example, we can take the tag Environment. We might expect tag Environment to have value Production, but users can enter Prod, proDucTion, Prd … or anything else. For end-user this doesn’t make a big difference, they will interpret it as a production anyway. But 1. it doesn’t look clean and nice and 2. if we are during some kind of automation on it, this can mess things up. For example, I like to automatically enable backups on VMs that have Tag Environment with value Production. I have that sorted out with Azure Policy where I only allow pre-defined values. But if we already have a mess, we need to clean it up.
To perform that one-time task automatically, you can use this simple PowerShell script:
The tag Name is not correct, but the Value needs to stay
We can easily get into this situation when we want to unify tags with the same purpose and give them the same name. As an example, we can use the tag Description. Very useful tag. And a very obvious one, that users tend to enter even without enforcement. The value of this tag will obviously be different every time, and it’s not something that we need to worry about. But the name can be entered as a Description, note, Desc, Notes, details, …
Cleaning will require keeping the value and replacing the tag names. I wrote a simple PowerShell script for that purpose as well:
Using Azure Resource Tags will make you think more about it and help you refine your tagging strategy. Do you have favorite tips or trick about using tags? Let me know!
Fun fact, writing this post, and using the example tags above was not only a coincidence. I’ve seen this in someone’s Azure yesterday and that made me write all of this :)
Thank you for visiting and keep clouding around.
Vukašin Terzić
